Recently, Assistant Professor Wang Chundong’s research group in SIST independently discovered a covert channel based on the fsync function within computer storage and named it Sync+Sync. The result was published in an article entitled “Sync+Sync: A Covert Channel Built on fsync with Storage”, and was accepted by USENIX Security 2024, one of the top four international conferences in the field of computer information security and privacy. Third-year master student Jiang Qisheng is the first author of the paper, and Prof. Wang Chundong is the corresponding author.
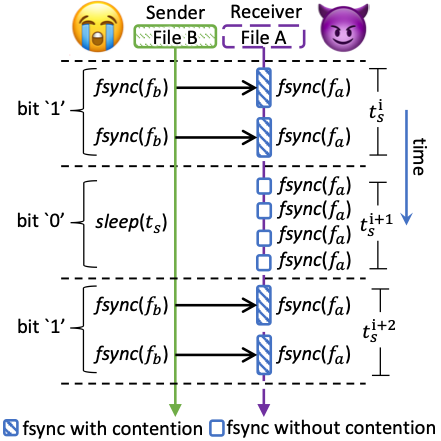
Scientists have built a variety of covert channels for secretive information transmission with CPU cache and main memory. In this paper, Wang’s group turned their focus to a lower level in the memory hierarchy—the persistent storage. Most programs store intermediate or final results in the form of files, and some of them call fsync function to synchronously persist a file with storage device for orderly persistence. A quantitative study showed that one program would undergo significantly longer response time for fsync call if the other program is concurrently calling fsync, although they do not share any data. Wang’s group further found that, concurrent fsync calls contend at multiple levels of storage stack due to sharing software structures and hardware resources.
To address the abovementioned issues, the group accordingly built a covert channel named Sync+Sync. The channel Sync+Sync delivers a transmission bandwidth of 20,000 bits per second at an error rate of about 0.40% with an ordinary solid-state drive. Sync+Sync can be conducted in cross-disk partition, cross-file system, cross-container, cross-virtual machine, and even cross-disk drive fashions, without sharing data between programs. In addition, Wang’s group launches side-channel attacks with Sync+Sync and manage to precisely detect operations of a victim database (e.g., insert/update and B-Tree node split). They also leverage Sync+Sync to distinguish applications and websites with high accuracy by detecting and analyzing their fsync frequencies and flushed data volumes. These attacks are useful to support further fine-grained information leakage.
This work was done by ShanghaiTech University. It was jointly supported by Nature Science Foundation of Shanghai and ShanghaiTech Startup Funding.
*This article is provided by Prof. Wang Chundong




 沪公网安备 31011502006855号
沪公网安备 31011502006855号


